While doing a bit of playing around with Hashicorp’s Terraform tutorial, I realized that I was being led to store secrets used to access my AWS account as a local environment variable.
My first question is how to retrieve them because if I can, so can anyone else who gains access to your machine. This doesn’t require admin access to retrieve. How many devs are storing their production keys as a local env variable? You could leverage your EDR solution or create a PowerShell script to test for their existence.
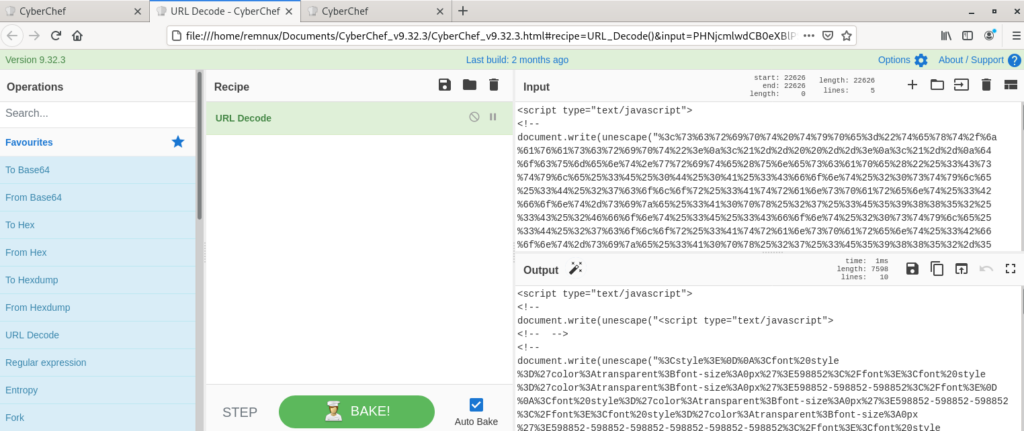
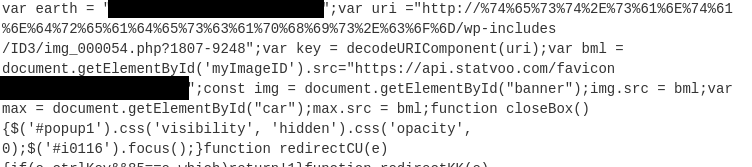
This script will let you return the secrets using a simple one-liner in PowerShell.

There has to be a better way, stay tuned for a future post.
Resource: https://docs.aws.amazon.com/cli/v1/userguide/cli-configure-envvars.html